Intro
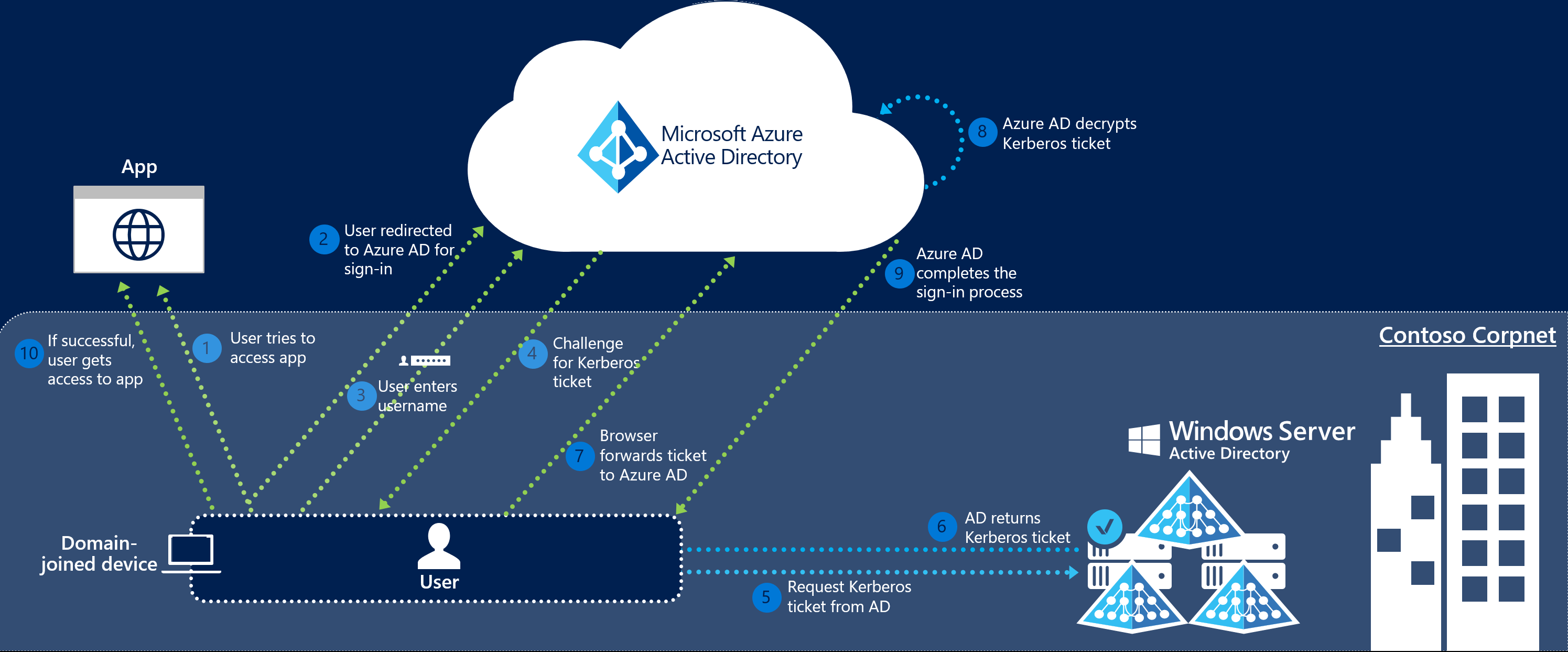
For personal use I have an Microsoft 365 tenant, and therefore also an Azure Active Directory (Recently renamed to Entra ID). I’ve also configured Azure AD Connect to sync with the local active directory (I know it’s legacy, but it’s nice for the lab). My family prefers to use one account for most of the used self hosted services. So I also wanted to enable SSO on my Synology NAS. But ran into some problems with account matching.
Handy information
After a lot of digging around and searching for logging in the Synology which actualy contains debug information, I’ve found an file where handy debug information is stored. The log file also contains SSO debugging information. The file is located in the (default linux logging) folder /var/log
/var/log/synoscgi.logThis file contains lots of logging for different DSM services. In the example below you can see the notification “no such user:” followed with an string, UPN, email or something else. It’s good to know that the username passed on by the SSO must exactly match the username as known in the DSM. In my case it must be an UPN DOMAIN\User.
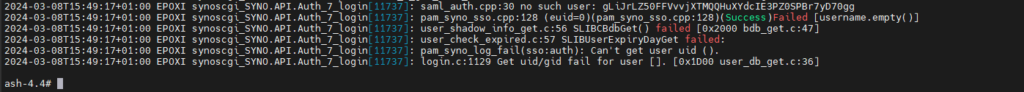
Live view of this view is possible with the command tail.
tail -f /var/log/synoscgi.logTags / keywords: Synology SSO Debugging Logging Microsoft 365 Azure Active Directory Entra ID
Accessing the file
When you want to access the file you need to SSH into the machine, SSH can be enabled by the following steps:
DSM > Control Panel > Terminal & SNMP > “Enable SSH service”
My advice here is to change the port, and do not port forward (or something similar) SSH of the NAS to the internet!