In my lab I automate (as far as it’s possible) everything, so also deployments for Microsoft (365 / Azure) cloud enviroments.
Intro
Regularly I have to set up or rebuild an environment for an new testing enviroment. With existing tools for powershell from Microsoft like, msgraph, connect-AzureAD, Connect-MsolService, Connect-MicrosoftTeams and more, a lot can be automated. Unfortanetly some specific things as enabling the “Customer Lockbox“, or disabling the “Bing Data Collection“, isn’t configurable with powershell and can only be done by the specified web portal.
So somewhere in my search trough the jungle I did read something on Stackoverflow, someone did try to use the hidden API behind Azure. Or in other words, he or she was trying to mimic the web portal buttons and actions.
While I had composed the correct restmod dataset I was struggeling to get it working, evertime I would get the 401 Unauthorized Notification. After a long search I came across the website of Jos Lieben from www.lieben.nu, he had written an Powershell script that acquires an API Token for an specific resource.
After some fiddeling with the script I managed to acquire the correct API key, to use for an settings in the Microsoft Admin center.
Step 1, Downloading scripts
First we need to download the code needed for our purpose, it can be downloaded following Github page. In that repository are 5 files, each file starting with API is an example script of the resource domain name later in the filename. We’ll come later to those resource domain names. Also there is an GenericAPITokenAcquire.ps1 and 365DisableBingDataCollection.ps1, the first file acquires the token, and is used in the second file. See it like an function file. So we can use it in more scripts, offcourse you could also run the Generic script and save the token somewhere, but that’s an security risk but also the token is related to the resource used then.
So for now save one of the API files, I’ll use the API main.iam.ad.ext.azure.com.ps1 in this case.
Step 2, Capturing the flag uhh Azure portal
Tip, To try the scripts in an test enviroment, request an Deverloper tenant from Microsoft. It’s filled with demo data, like users, groups and more so test can safely be done: https://developer.microsoft.com/en-us/microsoft-365/dev-program
For an example I want to disable the Self service password reset we go to the Azure portal.
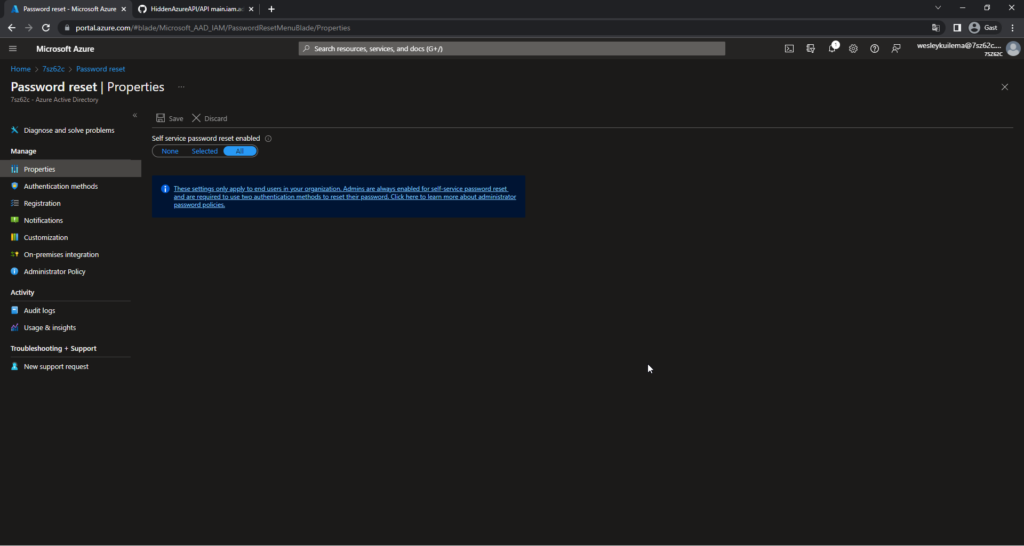
Wel will change the Self service password rest to None and Save it, there will appear some network packets on the inspect element toolset.
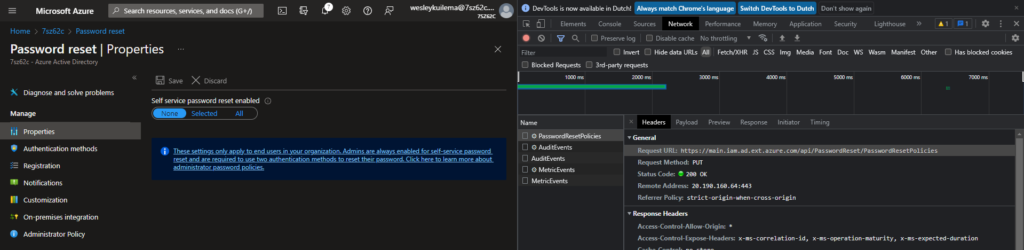
In this case we are searching for the PasswordResetPolicies network packet, open it an take a look an the Request URL: it contains the same URL as the name of our script. This URL is what the save button is talking to, we call it the endpoint, so all settings are PUT to that endpoint and saved. So in this case https://main.iam.ad.ext.azure.com is also our endpoint and therfore also our Resource, we need to use this domain to acquire an token later on. Almost everytime the URL without the filepath behind it is the Resource URL, other examples are: admin.microsoft.com, graph.microsoft.com, management.azure.com, admin.teams.microsoft.com.
When we open the payload tab we can see what settings are being send to the endpoint in JSON format.
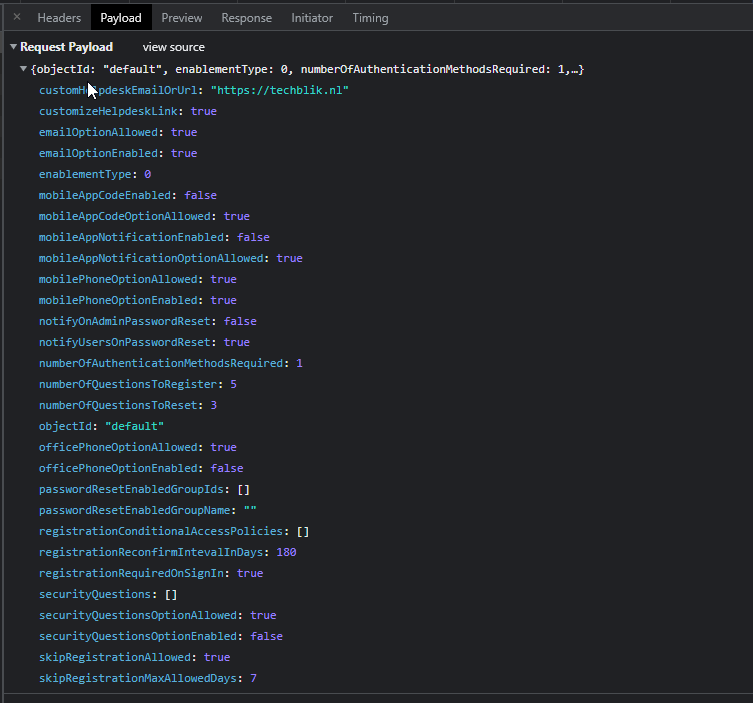
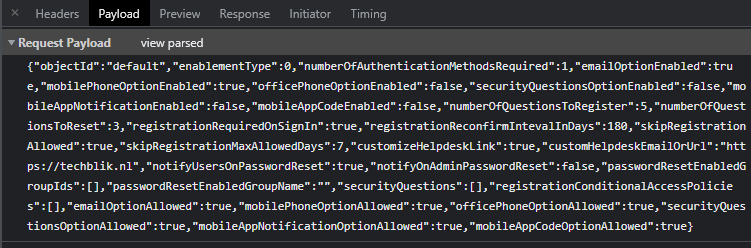
Source/Unformatted JSON, this string is more diffecult to read, but easier to use in the powershell script beceuse we can copy is 1:1
For now we need to copy this JSON and use it for step 3

Hallo Wesley,
Zie dat jij ook bezig bent met het automatiseren van het aanzetten van SSPR, heb jij toevallig ook pogingen gedaan om de optie weer uit te zetten en passwordResetEnabledGroupIds en passwordResetEnabledGroupName te resetten naar iets leegs?
Altijd leuk om jezelf tegen te komen. Inmiddels heb ik de juiste formatting gevonden. Het is echt puur een kwestie van de juiste JSON.